19 May 2021
Cybersecurity researcher Bertrand Milot gave a presentation on the state of cyber-piracy in Canada and around the world at the “Information Security in COVID Times (Sécurité de l’information en temps de COVID)” conference organized by Les Affaires on March 16, 2021. The portrait made by the founder of the cybersecurity firm Bradley & Rollins is chilling.
The pandemic has created a context where computer vulnerabilities have multiplied (through remote working and poor protection of computers and VPN networks), but also the vulnerability of Internet users, clicking on phishing emails thinking they will receive their screening results, have access to a miracle cure or a vaccine on the black market.
In March 2020, ReedSmith saw a 400% increase in scams in that month. In April 2020, Google blocked 18 million phishing and malware emails per day.
Even more worrisome, the attacks have intensified, become more complex… knowing that the pirates have also started to better organize themselves.
“We now see a real methodology of relate between organizations of cybercriminals, where an organization A offers its services of cybercrime to an organization B, to be exploited by the latter.”
Here is an example, taken from his lecture, where the criminal group announces its ransomware literally… “as a service” (SaaS)!
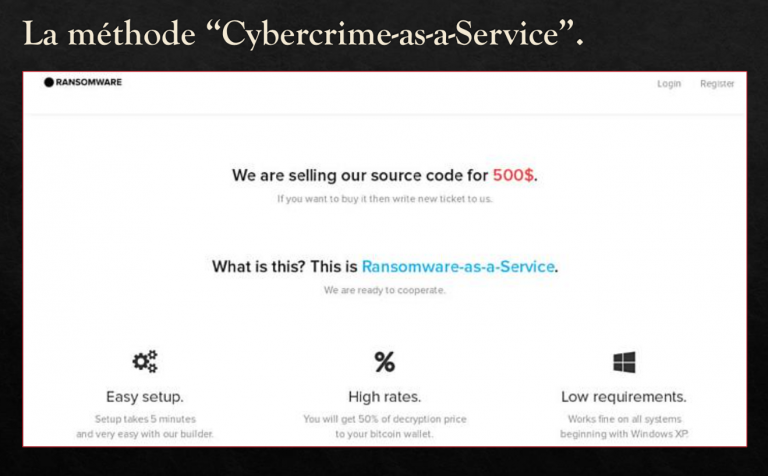
Companies are currently extremely vulnerable, says Betrand Milot.
“The only reason your company hasn’t been attacked yet is not that you’re well protected or lucky, it’s just that cybercriminals have a capacity problem. They can’t attack everyone.”
Do not pay to recover your data
An emerging threat is the famous “ransomware”. These malware blocks access to your files by encrypting them; hackers then ask for a sum of money – sometimes in Bitcoin – to unlock it. But there is no guarantee that they will if you pay!
A notable participant in the business conference was Louis-Philippe Desjardins, Senior Director of Cybersecurity at Deloitte, but also, and most importantly, Chief Information Security Officer at the STM, when the transit system suffered a ransom cyber attack, last November. The STM refused to pay $2.8 million to recover access to one third of its servers that had been encrypted.
“Paying is never plan A, says the Director of Cybersecurity. To have the freedom to make that decision, you have to have a good backup strategy and make sure you have everything you need to take back the organization.”
The STM was able to do so, after a laborious effort to relaunch.
The importance of making several backup copies, the famous “back-up” – incrementally, so staggered over time – and also in an isolated place in your network, is the strongest message that emerged from its presentation.
“There is a difference between having a backup and having a good backup strategy,” explained Philippe Desjardins. If you have a version in production, with a backup that is done every night and that is overwritten the next night, that is not enough. If you have a compromise and you only realize it 48 hours later, it will impact your backup copy. You have no built-in backup to restore in case of an incident.”
The Director of Cybersecurity advises to make incremental copies over several weeks and even months. It will then be possible. Om case of compromise, to restart your systems with a recent version “not corrupted”.
You know what you have to do… Good backup!




